How To Install and Configure OpenLDAP in Ubuntu 14.04 Server
Introduction
LDAP (Lightweight Directory Access Protocol) is a protocol designed to access and manage all information in a centralized, hierarchical file and directory structure so there are no need to manage all information on all systems.
The hierarchical structure is shows that how the data is related. It can be used to store any kind of information such as mail id, their personal details, login information and it is often used as one component of a centralized authentication system.
In this post, we will discuss how to install and configure an OpenLDAP server on an Ubuntu 14.04 server. We will discuss about installation steps of phpLDAPadmin for graphical interface and secure it through web.
Steps to Install and Configure OpenLDAP in Ubuntu
Before we start main LDAP software in ubuntu we need to install their dependency which is already added in ubuntu repository.
First there is a need to update apt repository so it can configure all added repository and fetch files from there.
sudo apt-get update sudo apt-get install slapd ldap-utils
The above step will update repository of your ubuntu server and then install slapd and ldap utilities which required for OpenLDAP.
This will install default configuration for ldap so there is a need to reconfigure setting for your server.
Reconfigure Slapd specific for your server
Slapd package installation skips important configuration questions so there is a need to reconfigure it so we can enter our specific configuration as per our server We can gain access to all of the prompts though by telling our system to reconfigure the package:
sudo dpkg-reconfigure slapd
Below are few new questions that will be asked as you go through this process. Let’s go over these now:
- Omit OpenLDAP server configuration? No
- DNS domain name?
- This option will determine the base structure of your directory path. Here you can enter domain name of your server.
- For this guide, we’re going to select linuxtweaks.infor our configuration.
- Organization name?
- This is entirely up to your preferences.
- For this guide, we will be using linuxtweaks as the name of our organization.
- Administrator password?
- As I mentioned in the installation section, this is your real opportunity to select an administrator password. Anything you select here will overwrite the previous password you used.
- Database backend? HDB
- Remove the database when slapd is purged? No
- Move old database? Yes
- Allow LDAPv2 protocol? No
At this point, your LDAP should be configured in a fairly reasonable way.
Install phpLDAPadmin to Manage LDAP using Web
Although it is very possible to administer LDAP through the command line, most users will find it easier to use a web interface. phpLDAPadmin is an web interface for managing LDAP configuration which provides more functionality and to help remove some of the friction of learning the LDAP tools.
The Ubuntu repositories contain the phpLDAPadmin package. You can install it by typing:
sudo apt-get install phpldapadmin
This should install the administration interface, enable the necessary Apache virtual hosts files, and reload Apache.
The web server is now configured to serve your application, but we will make some additional changes. We need to configure phpLDAPadmin to use the domain schema as we had configured for LDAP, and we are also going to make it secure our configuration a little bit.
phpLDAPadmin Configuration
Now that the package is installed, we need to configure it so that it can connect with the LDAP directory structure that was created during the OpenLDAP configuration stage.
Begin by opening the main configuration file with root privileges in your text editor:
vi /etc/phpldapadmin/config.php
In this file, we need to add the configuration details that we set up for our LDAP server. Start by looking for the host parameter and setting it to your server’s domain name or public IP address. This parameter should reflect the way you plan on accessing the web interface:
$servers->setValue('server','host','server_domain_name_or_IP');
Next up, you’ll need to configure the domain name you selected for your LDAP server. Here you have to search setvalue with dc configuration. Remember, in our example we selected linuxtweaks.in. We need to translate this into LDAP syntax by replacing each domain component (everything not a dot) into the value of a dc specification.
All this means is that instead of writing linuxtweaks.in, we will write something like dc=linuxtweaks,dc=in. We should find the parameter that sets the server base parameter and use the format we just discussed to reference the domain we decided on:
$servers->setValue('server','base',array('dc=test,dc=com'));
Now we need to adjust this same thing in our login bind_id parameter. The cn parameter is already set as “admin”. This is correct. We just need to adjust the dc portions again, just as we did above:
$servers->setValue('login','bind_id','cn=admin,dc=linuxtweaks,dc=in');
The last thing that we need to adjust is a setting that control the visibility of warning messages. By default phpLDAPadmin will throw quite a few annoying warning messages in its web interface about the template files that have no impact on the functionality.
We can hide these by searching for the hide_template_warning parameter, uncommenting the line that contains it, and setting it to “true”:
$config->custom->appearance['hide_template_warning'] = true;
You can save and close the file when you are finished by pressing :x
Secure Web interface using SSL
We want to secure our connection to the LDAP server with SSL so that outside parties cannot intercept our communications.
To do this, we need to set up a self-signed SSL certificate that our server can use. We can also use a purchased SSL certificate but if we don’t have then we can also use self-signed certificate which will not help us validate the identity of the server, but it will allow us to encrypt our messages.
The OpenSSL packages should be installed on your system by default if not then need to install it.
apt-get install openssl
First, we should create a directory to hold our certificate and key.
sudo mkdir /etc/apache2/ssl
Next need to generate ssl for ldap interface
sudo openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout /etc/apache2/ssl/linuxtweaks.key -out /etc/apache2/ssl/linuxtweaks.crt
You will have to answer some questions in order for the utility to fill out the fields in the certificate correctly. The only one that really matters is the prompt that says Common Name . Enter your server’s domain name or IP address which you want to make secure.
When you are finished, your certificate and key will be written to the /etc/apache2/ssl directory.
Now there is a need to configure phpLDAPadmin for apache.
phpLDAPadmin Modification in Apache Configuration
The first thing we will do is modify the alias that is set up to serve our phpLDAPadmin files.
Open the file with root privileges in your text editor:
sudo vi /etc/phpldapadmin/apache.conf
This is the place where we need to decide on the URL location for accessing our ldap web interface such as phpldap. The default is /phpldapadmin, but we want to change this to cut down on random login attempts by bots and malicious parties.
For this guide, we’re going to use the location /linuxtweaksldap, but you should choose your own value.
We need to modify the line that specifies the Alias. This should be in an IfModule mod_alias.c block. When you are finished, it should look like this:
<IfModule mod_alias.c>
Alias /linuxtweaksldap /usr/share/phpldapadmin/htdocs
</IfModule>
When you are finished, safe and close the file by pressing :x
HTTP Virtual Host Configuration
Next, we need to modify our current Virtual Hosts file. Open it with root privileges in your editor:
sudo vi /etc/apache2/sites-enabled/000-default.conf
Inside, you’ll see a rather bare configuration file that looks like this:
<VirtualHost *:80>
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
</VirtualHost>
Here we want to add our domain name or ip address of our server and setup redirect to point all http request to https interface for security purpose.
The changes we discussed will end up looking like this.
<VirtualHost *:80>
ServerAdmin webmaster@server_domain_or_IP
DocumentRoot /var/www/html
ServerName server_domain_or_IP
Redirect permanent /linuxtweaksldap https://server_domain_or_IP/linuxtweaksldap
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
</VirtualHost>
Here server_domain_or_IP should be the same which is configured in SSL creation and ldap configuration.
Save and close the file when you are finished.
Configure the HTTPS Virtual Host File
Apache includes a default SSL Virtual Host file. However, it is not enabled by default.
We can enable it by typing:
sudo a2ensite default-ssl.conf
This will link the file from the sites-available directory into the sites-enabled directory. We can edit this file now by typing:
sudo vi /etc/apache2/sites-enabled/default-ssl.conf
First of all, set the ServerName value to your server’s domain name or IP address again and change the ServerAdmin directive as well:
ServerAdmin webmaster@server_domain_or_IP ServerName server_domain_or_IP
Next, we need to set the SSL certificate directives to point to the key and certificate that we created.
SSLCertificateFile /etc/apache2/ssl/linuxtweaks.crt SSLCertificateKeyFile /etc/apache2/ssl/linuxtweaks.key
Save and close the file when you are finished.
Restart Apache to implement all of the changes that we have made:
sudo service apache2 restart
Log in Page of phpLDAPadmin Web Interface
We have made the configuration changes we need to the phpLDAPadmin software. We can now begin to use it.
We can access the web interface by visiting our server’s domain name or public IP address followed by the alias we configured. In our case, this was /linuxtweaksldap:
http://server_domain_name_or_IP/linuxtweaksldap
The first time you visit, you will probably see a warning about the site’s SSL certificate.
Just click on Proceed anyway as this is self signed certificate.
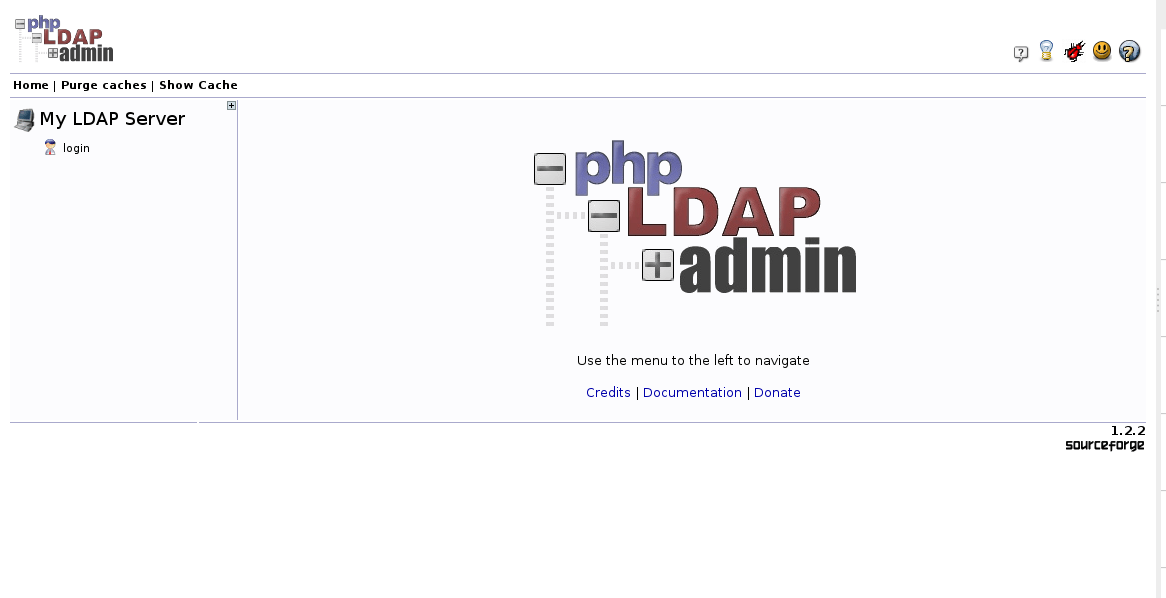
You will see the main phpLDAPadmin landing page:
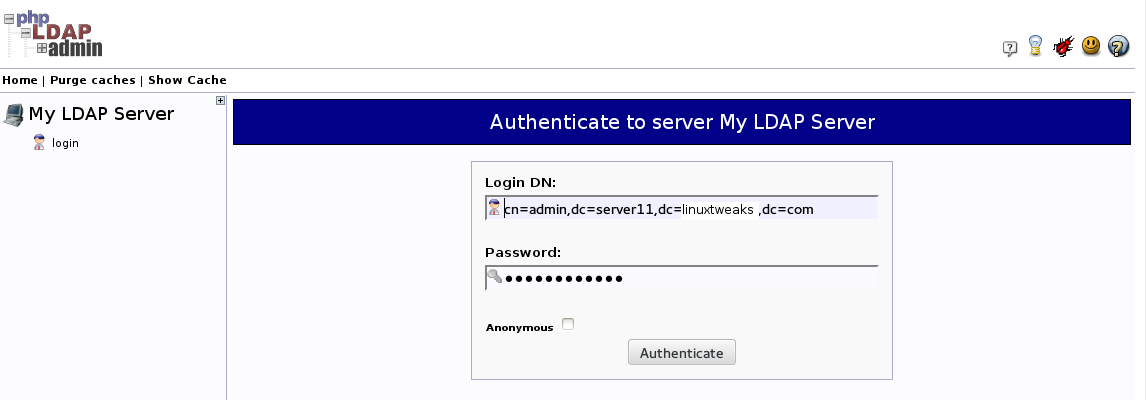
Click on the “login” link that you can see on the left-hand side of the page.
You will be taken to a login prompt. The login “DN” is like the username that you will be using. It contains the account name under “cn” and the domain name you selected for the server broken into “dc” sections as we described above.
It should be pre-populated with the correct value for the admin account if you configured phpLDAPadmin correctly. In our case, this looks like this:
cn=admin,dc=linuxtweaks,dc=in
For the password, enter the administrator password that you configured during the LDAP configuration.
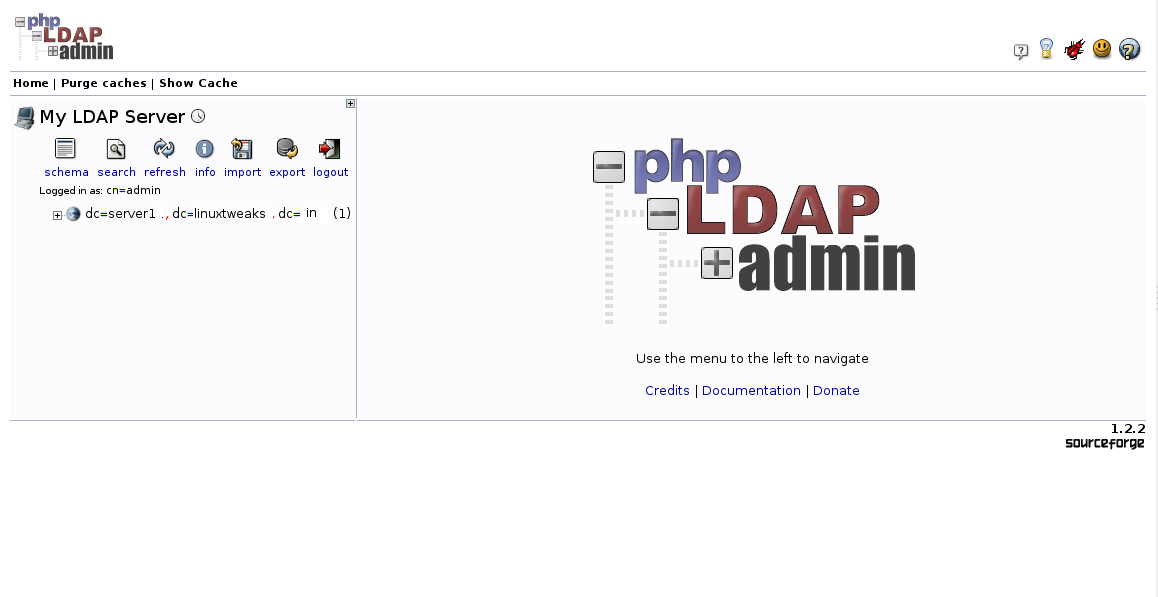
You will be taken to the main interface:
Add Organizational Units, Users, Groups & Mail-ids
At this point, you are logged into the phpLDAPadmin interface. You have the ability to add users, organizational units, groups & their relationships.
LDAP is flexible in how you wish to structure your data and directory hierarchies. You can basically create whatever kind of structure you’d like and create rules for how they interact.
Conclusion
You should now have OpenLDAP installed and configured on your Ubuntu 14.04 server. You have also installed and configured a web interface to manage your structure through the phpLDAPadmin program. Have configured basic security for web interface using SSL self signed certificate and apache to forcely use secure data transfer.
The system that we have set up is quite flexible and you should be able to design your own organizational schema and manage groups of resources as your needs demand. In the next guide, we’ll discuss how to configure your networked machines to use this LDAP server for system authentication.